While the Health Insurance Portability and Accountability Act (HIPAA) Security Rule aims to safeguard health information, some may question its scope and the types of information it covers. In this article, we will provide a comprehensive overview of the types of health information addressed by the Security Rule. By examining the administrative, physical, and technical safeguards for electronic health information, we aim to dispel any doubts and ensure a clear understanding of the rule’s impact on protecting sensitive healthcare data.
Key Takeaways
- The Security Rule covers electronic protected health information (ePHI), which includes electronic medical records, digital images, laboratory results, and other electronic data linked to an individual’s health.
- Individually identifiable health information, such as names, addresses, social security numbers, and medical record numbers, is also covered by the Security Rule.
- The Security Rule aims to protect the privacy and security of these types of health information by ensuring confidentiality, integrity, and availability of the data.
- The Security Rule requires organizations to implement administrative, physical, and technical safeguards to protect ePHI, including workforce training programs, risk assessments, access controls, data encryption, and regular software updates.
Types of Health Information Covered by the Security Rule
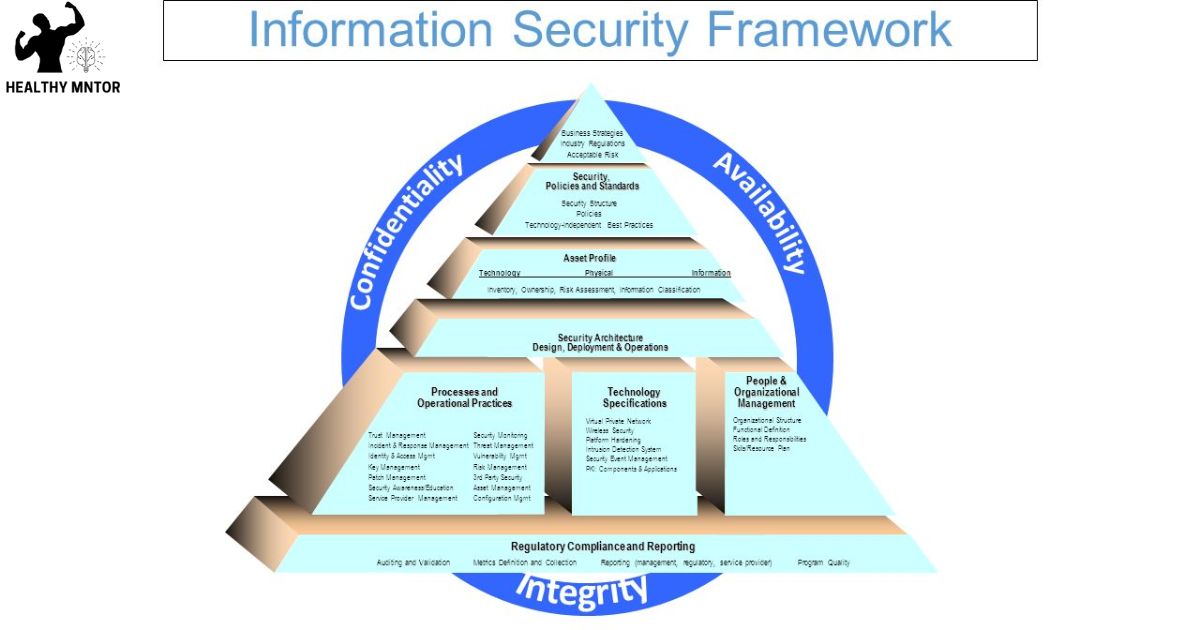
The Security Rule’s coverage extends to various types of health information, including electronic protected health information (ePHI) and individually identifiable health information. ePHI refers to any health information that is stored, transmitted, or received electronically. This includes electronic medical records, digital images, laboratory results, and any other electronic data that can be linked to an individual’s health. Individually identifiable health information, on the other hand, is any information that can be used to identify a specific individual and is related to their past, present, or future physical or mental health condition. This can include names, addresses, social security numbers, medical record numbers, or any other information that can be used to identify a person in the context of their health information. The Security Rule aims to protect the privacy and security of these types of health information to ensure the confidentiality, integrity, and availability of the data.
Safeguards for Electronic Protected Health Information (ePHI
To ensure the security of electronic protected health information (ePHI), organizations must implement appropriate safeguards and regularly assess their effectiveness. The following measures can help organizations protect ePHI and maintain compliance with the Security Rule:
- Administrative Safeguards: These are policies and procedures that govern the management of ePHI, such as implementing workforce training programs, conducting regular risk assessments, and establishing a contingency plan for emergencies.
- Physical Safeguards: These controls focus on the physical protection of ePHI, including securing facilities, controlling access to electronic systems, and implementing measures to prevent unauthorized access, theft, or damage to electronic devices.
- Technical Safeguards: These measures involve the use of technology to protect ePHI, such as implementing access controls, encrypting data, and regularly updating and patching software.
Administrative Requirements for Health Information Security
Effective health information security relies on organizations adhering to the administrative requirements outlined in the Security Rule, which include implementing workforce training programs and regularly conducting risk assessments. These administrative requirements play a crucial role in ensuring the confidentiality, integrity, and availability of health information. Workforce training programs are essential in educating employees on their responsibilities regarding the security of health information. This includes training on identifying and reporting security incidents, as well as understanding the importance of password management and access control. Regular risk assessments are also vital in identifying potential vulnerabilities and implementing appropriate safeguards to mitigate risks. Organizations must assess risks to their health information systems and evaluate the effectiveness of their security measures. By adhering to these administrative requirements, organizations can strengthen their health information security posture and protect sensitive patient data from unauthorized access or disclosure.
Physical Security Measures for Protecting Health Information
How can organizations implement physical security measures to protect health information? When it comes to safeguarding sensitive health information, organizations must prioritize implementing robust physical security measures. Here are three key steps that can help ensure the protection of health information:
- Access Control: Organizations should implement access control measures such as biometric authentication, key cards, or security guards to restrict physical access to areas where health information is stored or processed. This helps prevent unauthorized individuals from gaining access to sensitive data.
- Surveillance Systems: Installing surveillance systems, including CCTV cameras and alarms, can deter potential intruders and provide real-time monitoring of sensitive areas. Organizations can also consider using motion sensors and intrusion detection systems to enhance security.
- Secure Storage: Health information should be stored in secure locations, such as locked cabinets or data centers with restricted access. Additionally, organizations should implement measures like encryption and regular backups to protect health information from theft or loss.
Technical Safeguards for Electronic Health Information
Our organization utilizes technical safeguards to ensure the security and confidentiality of electronic health information. Technical safeguards refer to the technology and methods used to protect electronic health information from unauthorized access, alteration, or destruction. These safeguards are an integral part of the HIPAA Security Rule, which establishes the standards for protecting electronic health information. Some of the key technical safeguards include access controls, audit controls, integrity controls, transmission security, and encryption. Access controls ensure that only authorized individuals can access electronic health information. Audit controls track and record any activity related to electronic health information. Integrity controls protect against unauthorized alterations or deletions of electronic health information. Transmission security safeguards the transmission of electronic health information over open networks. Encryption is the process of converting electronic health information into a code to prevent unauthorized access. By implementing these technical safeguards, our organization ensures the security and confidentiality of electronic health information, giving our audience the confidence that their personal health information is well-protected.
Flexibility in Implementing the Security Rule
There are several key areas where flexibility is allowed in implementing the Security Rule, such as the implementation specifications and the risk analysis process. This flexibility allows covered entities to tailor their security measures to their specific needs and circumstances. Here are three areas where flexibility is particularly important:
- Implementation Specifications: The Security Rule provides a set of implementation specifications that covered entities must meet. However, these specifications are not one-size-fits-all. Covered entities have the flexibility to determine the most appropriate and reasonable measures to implement based on their size, complexity, and resources.
- Risk Analysis Process: The Security Rule requires covered entities to conduct a risk analysis to identify potential vulnerabilities and risks to the confidentiality, integrity, and availability of their electronic protected health information. This risk analysis process allows covered entities to assess their unique risks and develop tailored security measures accordingly.
- Administrative Safeguards: The Security Rule recognizes that administrative safeguards may vary depending on the covered entity’s organizational structure and resources. Flexibility is provided to accommodate different approaches to safeguarding health information, as long as the overall goal of protecting the confidentiality and integrity of the information is achieved.
Risk Assessment and Documentation Requirements for Compliance
Covered entities must conduct a thorough risk assessment and maintain comprehensive documentation in order to comply with the Security Rule. The risk assessment process involves identifying and analyzing potential risks to the confidentiality, integrity, and availability of electronic protected health information (ePHI). This includes assessing the likelihood and impact of potential threats, vulnerability to those threats, and the effectiveness of current security measures. The documentation requirements include documenting the risk assessment findings, the security measures implemented to mitigate identified risks, and any decisions made regarding the acceptance or mitigation of risks. Additionally, covered entities must maintain documentation of security policies and procedures, training materials, and any security incidents or breaches. This documentation is crucial for demonstrating compliance with the Security Rule and can also serve as a valuable reference for ongoing security management and improvement efforts.
Frequently Asked Questions
How Does the Security Rule Address the Protection of Patient’s Mental Health Information?
The security rule addresses the protection of all types of health information, including mental health information. It sets standards and safeguards to ensure the confidentiality, integrity, and availability of patient data, including mental health records.
Are There Any Specific Requirements or Safeguards for the Security of Health Information Stored in Cloud-Based Systems?
Cloud-based systems that store health information must adhere to specific requirements and safeguards outlined in the Security Rule. These measures ensure the protection, confidentiality, integrity, and availability of sensitive patient data within the cloud environment.
What Are the Consequences for Healthcare Organizations That Fail to Comply With the Security Rule?
Failure to comply with the Security Rule can have significant consequences for healthcare organizations, including fines, penalties, and reputational damage. It is crucial for organizations to implement the required safeguards to protect health information and mitigate the risks of non-compliance.
Does the Security Rule Address the Security of Health Information Transmitted Through Mobile Devices?
The Security Rule addresses the security of health information transmitted through mobile devices. It outlines measures to protect the confidentiality, integrity, and availability of electronic protected health information (ePHI) when accessed, stored, or transmitted using mobile devices.
Are There Any Specific Guidelines or Recommendations for Healthcare Organizations to Follow When Conducting a Risk Assessment for Compliance With the Security Rule?
Healthcare organizations must conduct a risk assessment to ensure compliance with the Security Rule. Specific guidelines and recommendations exist to guide them in this process. This helps protect the confidentiality, integrity, and availability of health information.
Conclusion
In conclusion, the Security Rule addresses various types of health information, including electronic protected health information (ePHI). It sets forth safeguards to protect ePHI, such as administrative requirements, physical security measures, and technical safeguards. The Security Rule allows flexibility in implementing these measures based on an organization’s unique circumstances. A hypothetical example demonstrating the importance of the Security Rule could be a healthcare provider experiencing a data breach due to inadequate technical safeguards, resulting in the exposure of patients’ sensitive medical information.